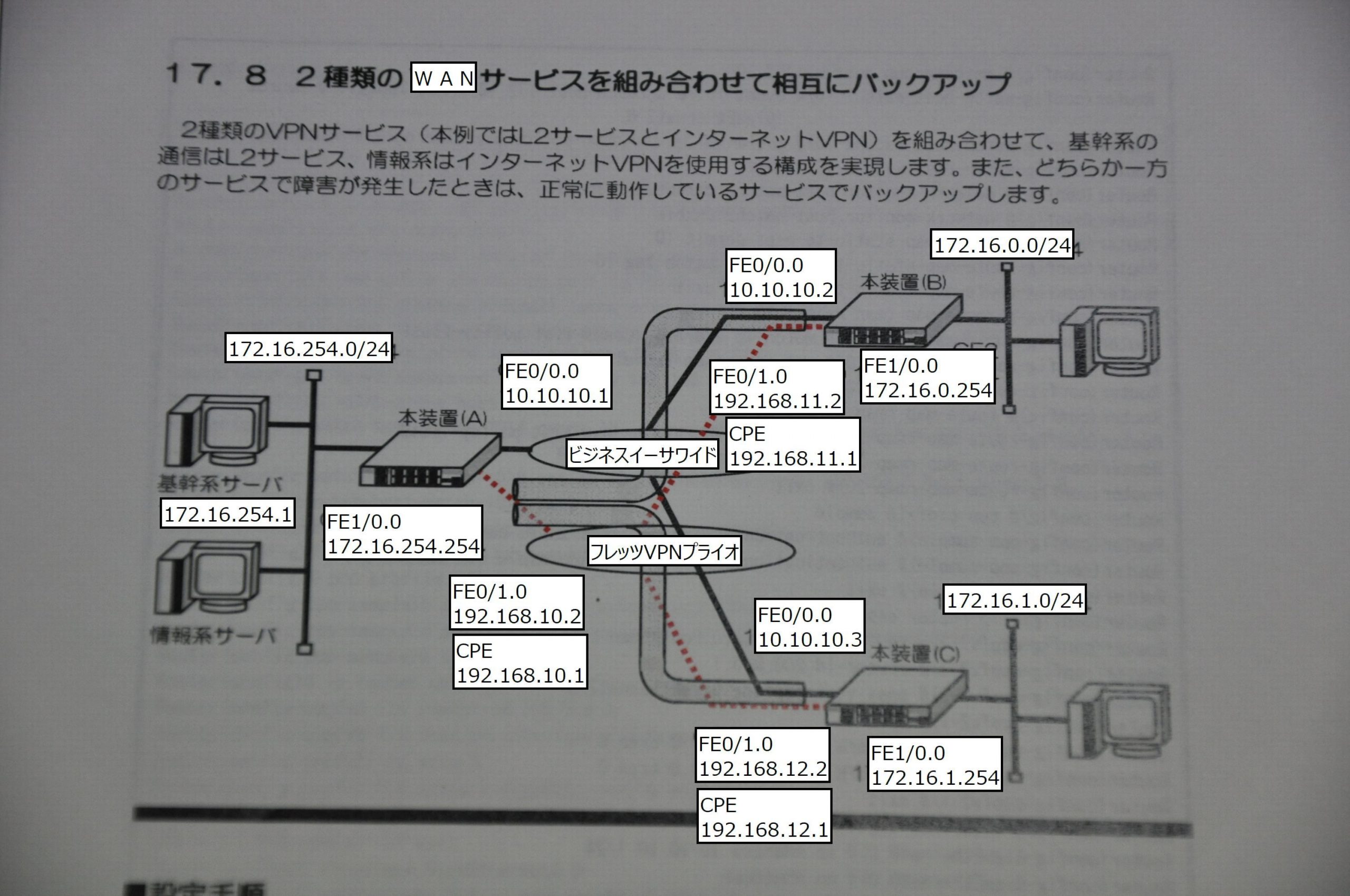
2種類のWANサービスを組み合わせて相互にバックアップ(NEC IX2025)

NEC IXルータ設定事例集を参考に、検証ネットワークを作成してみました。
IPアドレス、インターフェース名は上記のように変更させていただきました。CPEはフレッツVPNプライオの専用ルータで、NGN網端に配置します(NGN網内はIPv6で通信しますが、ユーザ側はIPv4で通信します)。
hostname RT-A
【本装置(A)のconfig】
ip route 192.168.0.0/16 192.168.10.1
ip route 172.16.0.0/24 Tunnel0.0 distance 120
ip route 172.16.1.0/24 Tunnel1.0 distance 120
ip route 172.16.254.1/32 FastEthernet1/0.0 tag 10
ip access-list policy-list1 deny ip src 172.16.254.1/32 dest 172.16.0.0/24
ip access-list policy-list1 permit ip src any dest 172.16.0.0/24
ip access-list policy-list2 deny ip src 172.16.254.1/32 dest 172.16.1.0/24
ip access-list policy-list2 permit ip src any dest 172.16.1.0/24
ip access-list sec-list permit ip src any dest any
ip ufs-cache enable
ike proposal ike-prop encryption aes hash sha
ike policy ike-policy1 peer 192.168.11.2 key himitsu ike-prop
ike policy ike-policy2 peer 192.168.12.2 key himitsu ike-prop
ipsec autokey-proposal ipsec-prop esp-aes esp-sha
ipsec autokey-map ipsec-policy1 sec-list peer 192.168.11.2 ipsec-prop
ipsec local-id ipsec-policy1 172.16.254.0/24
ipsec remote-id ipsec-policy1 172.16.0.0/24
ipsec autokey-map ipsec-policy2 sec-list peer 192.168.12.2 ipsec-prop
ipsec local-id ipsec-policy2 172.16.254.0/24
ipsec remote-id ipsec-policy2 172.16.1.0/24
watch-group host-watch1 10
event 10 ip unreach-host 172.16.0.254 Tunnel0.0 source FastEthernet1/0.0
action 10 ip shutdown-policy FastEthernet1/0.0 route-map-seq 10
action 20 turn-BAK-LED-on
exit
network-monitor host-watch1 directed-response
network-monitor host-watch1 enable
watch-group host-watch2 10
event 10 ip unreach-host 172.16.1.254 Tunnel1.0 source FastEthernet1/0.0
action 10 ip shutdown-policy FastEthernet1/0.0 route-map-seq 20
action 20 turn-BAK-LED-on
exit
network-monitor host-watch2 directed-response
network-monitor host-watch2 enable
route-map static-to-ospf permit 10
match tag 10
exit
route-map rmap permit 10
match ip address access-list policy-list1
set interface Tunnel0.0
exit
route-map rmap permit 20
match ip address access-list policy-list2
set interface Tunnel1.0
exit
ip router ospf 1
redistribute static route-map static-to-ospf
router-id 200.0.0.1
passive-interface FastEthernet1/0.0
area 0
network FastEthernet0/0.0 area 0
network FastEthernet1/0.0 area 0
exit
interface FastEthernet0/0.0
ip address 10.10.10.1/24
no shutdown
interface FastEthernet1/0.0
ip address 172.16.254.254/24
ip policy route-map rmap
no shutdown
interface FastEthernet0/1.0
ip mtu 1444
ip address 192.168.10.2/24
no shutdown
interface Tunnel0.0
tunnel mode ipsec
ip unnumbered FastEthernet1/0.0
ipsec policy tunnel ipsec-policy1 out
no shutdown
interface Tunnel1.0
tunnel mode ipsec
ip unnumbered FastEthernet1/0.0
ipsec policy tunnel ipsec-policy2 out
no shutdown
hostname RT-B
【本装置(B)のconfig】
ip route 192.168.0.0/16 192.168.11.1
ip route 172.16.254.0/24 Tunnel0.0
ip access-list sec-list permit ip src any dest any
ip ufs-cache enable
ike proposal ike-prop encryption aes hash sha
ike policy ike-policy peer 192.168.10.2 key himitsu ike-prop
ipsec autokey-proposal ipsec-prop esp-aes esp-sha
ipsec autokey-map ipsec-policy sec-list peer 192.168.10.2 ipsec-prop
ipsec local-id ipsec-policy 172.16.0.0/24
ipsec remote-id ipsec-policy 172.16.254.0/24
watch-group host-watch 10
event 10 ip unreach-host 172.16.254.254 Tunnel0.0 source FastEthernet1/0.0
action 10 ip shutdown-route 172.16.254.0/24 Tunnel0.0
action 20 turn-BAK-LED-on
exit
network-monitor host-watch directed-response
network-monitor host-watch enable
ip router ospf 1
router-id 200.0.0.2
passive-interface FastEthernet1/0.0
area 0
network FastEthernet0/0.0 area 0
network FastEthernet1/0.0 area 0
exit
interface FastEthernet0/0.0
ip address 10.10.10.2/24
no shutdown
interface FastEthernet1/0.0
ip address 172.16.0.254/24
no shutdown
interface FastEthernet0/1.0
ip mtu 1444
ip address 192.168.11.2/24
no shutdown
interface Tunnel0.0
tunnel mode ipsec
ip unnumbered FastEthernet1/0.0
ipsec policy tunnel ipsec-policy out
ip tcp adjust-mss auto
no shutdown
hostname RT-B
【本装置(C)のconfig】
ip route 192.168.0.0/16 192.168.12.1
ip route 172.16.254.0/24 Tunnel0.0
ip access-list sec-list permit ip src any dest any
ike proposal ike-prop encryption aes hash sha
ike policy ike-policy peer 192.168.10.2 key himitsu ike-prop
ipsec autokey-proposal ipsec-prop esp-aes esp-sha
ipsec autokey-map ipsec-policy sec-list peer 192.168.10.2 ipsec-prop
ipsec local-id ipsec-policy 172.16.1.0/24
ipsec remote-id ipsec-policy 172.16.254.0/24
watch-group host-watch 10
event 10 ip unreach-host 172.16.254.254 Tunnel0.0 source FastEthernet1/0.0
action 10 ip shutdown-route 172.16.254.0/24 Tunnel0.0
action 20 turn-BAK-LED-on
exit
network-monitor host-watch directed-response
network-monitor host-watch enable
ip router ospf 1
router-id 200.0.0.3
passive-interface FastEthernet1/0.0
area 0
network FastEthernet0/0.0 area 0
network FastEthernet1/0.0 area 0
exit
interface FastEthernet0/0.0
ip address 10.10.10.3/24
no shutdown
interface FastEthernet1/0.0
ip address 172.16.1.254/24
no shutdown
interface FastEthernet0/1.0
ip mtu 1444
ip address 192.168.12.2/24
no shutdown
interface Tunnel0.0
tunnel mode ipsec
ip unnumbered FastEthernet1/0.0
ipsec policy tunnel ipsec-policy out
ip tcp adjust-mss auto
no shutdown
ノンインテリジェントL2スイッチを疑似的なビジネスイーサワイド(WAN1)、L3スイッチを疑似的なフレッツVPNプライオ(WAN2)に見立てました。WAN1がダウンすればWAN2に迂回しますし、WAN2がダウンすればWAN1に迂回することを確認しました。しかし、なぜそうなるのか?という根本的な技術について、まだ理解が追い付いていません(汗)。